
Special Feature:
Mike Lemons – Vintara’s Director of Security Engineering, discusses key steps to implementing an Integrated Security System (ISS)
Summary:
Physical security; guns, guards, gates, incidents, and investigations were the daily bread of the typical pre 9/11 security executive. The daily bread of the typical IT director was protecting networks, privacy issues, backups, and restorations. Two separate universes operating as independent organizations run by completely separate departments. Convergence of these two separate universes after 9/11 has significantly changed the security industry. An enterprise’s cyber space and IT security and it’s physical security are now inalterably interrelated. This issue of Standard Wire will outline the key steps of implementing an integrated security management system reflecting the management of risk in these converging universes. This will be done by answering these five key questions:
First: What is Convergence?
Convergence means the integration the enterprise’s security infrastructure, enabling interoperability between physical and IT security technologies. This integration and interoperability occurs at four distinct levels:
Examples of Physical and IT elements of convergence include:
| Physical Security | IT Security |
| Controlled Access | Password Aging |
| Pass Cards | Virus Protection |
| Biometric Scanners | User Authentication |
| 24x7x365 Video Survellance | NSCA Certified Firewalls |
| 24x7x365 Guards | Clustered Servers |
| 24x7x365 Activity Logs | Denial of Service Protection |
| Logged Visitors' lists | Redundant Fail-Over |
| Fire Protection, VESDA & FM200 | Hot Swappable Components |
| Continuous Power Supply | Offsite Data Backup |
Second: What are the key characteristics of an Integrated Security System (ISS)?
SPECIAL FEATURE
Mike Lemons: Vintara, Director of Security Engineering
Mike has over 15 years of experience ranging in the areas of quality management, consulting, support services, security, and documentation. As a Quality Engineer for Solectron he decreased the average pre-manufacturing set-up time for Solectron’s 6,000 employees from 18 hours to 2 hours per employee. Mike has developed, implemented, and installed CAD/CAM enterprise solutions at major facilities world wide. He has managed teams of software engineers, professional service engineers, and pre-sales engineers on Fortune 500 accounts including Agere, Honeywell, Solectron, Jabil, Sanmina/SCI, and Eaton to develop custom solutions. His Process Skills include ECO, ECR, QMS, Document Control, PLM, Sarbanes-Oxley, ISO 9000, ISO 17799, C-TPAT, and Security Management Systems. Mike has a BS degree in Industrial and Manufacturing Engineering from Cal Poly, San Luis Obispo, CA
Regarding convergence and the implementation of an ISS, Mr. Lemons stated:
“Given we understand what convergence means and what are the critical characteristics of an Integrated Security System, the daunting task of developing and implementing an ISS can be distilled in several key steps. Bear in mind, any such implementation should utilize a Plan-Do-Check-Act (PDCA) methodology with a particular focus on the enterprise’s regulatory environment. The eight key steps to a successful implementation are:
Fourth: How can an ISS be quickly and cost effectively implemented?
The key to an effective and rapid implementation of the ISS is to automate and streamline the security processes as much as possible. The enterprise needs the ability to manage information, equipment, personnel, and incidents happening globally within a centralized database. Automated security systems can actively or passively gather information, spot trends, complete investigations, and drive necessary procedural and policy improvements. An ISS is dynamic, real-time, and global data with real-time access to global performance data from one central location. An ISS provides Directors with the ability to manage key performance activities and drill down to the situational information.
Fifth: How can Vintara help?
Vintara’s Enterprise Security Portal (VESP) gives an enterprise the ability to manage information, equipment, personnel and incidents happening globally within a centralized database. With VESP manages the information, spot trends, tracks incidents and investigations, while driving necessary procedural and policy improvements. VESP is a complete software solution and security portal. The platform successfully handles the convergence of physical security and IT security, moving clients from a localized static and reactive environment, to one that is dynamic, real-time, and global with real-time access to global performance data from one central location. VESP fosters closer internal communication within the organization by providing all stakeholders with an easy-to-use interface. Dashboards allow stakeholder to manage key performance activities and drill down to the situational information.
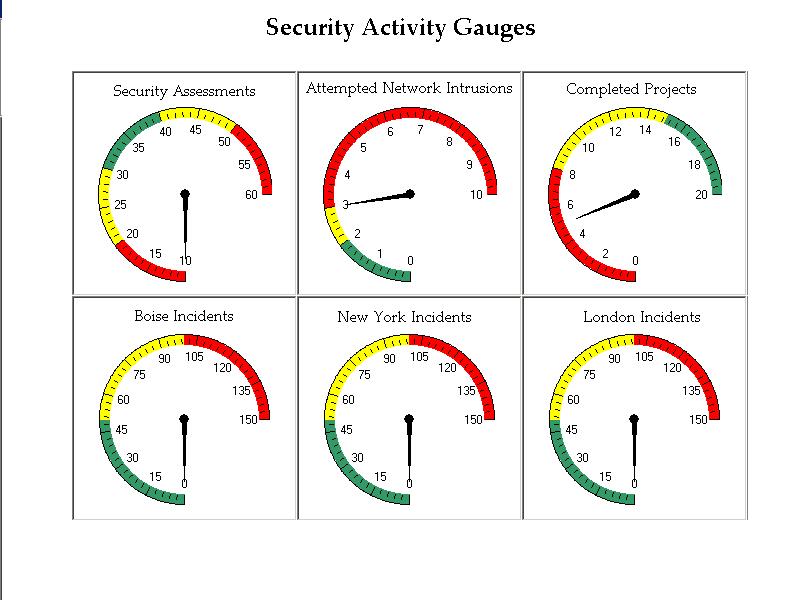
VESP modules include:
Strategic Planning
Assessment
Improvement
Policy
Review
Visit at http://security.vintara.com